AppQue
AppQue is classified as a Potentially Unwanted Program (PUP) due to its questionable distribution methods and undesirable functionalities. PUPs like AppQue are often installed on systems alongside other unwanted and potentially harmful programs, highlighting the need for caution when downloading software.
AppQue May Carry Out Various Intrusive Actions Once Installed
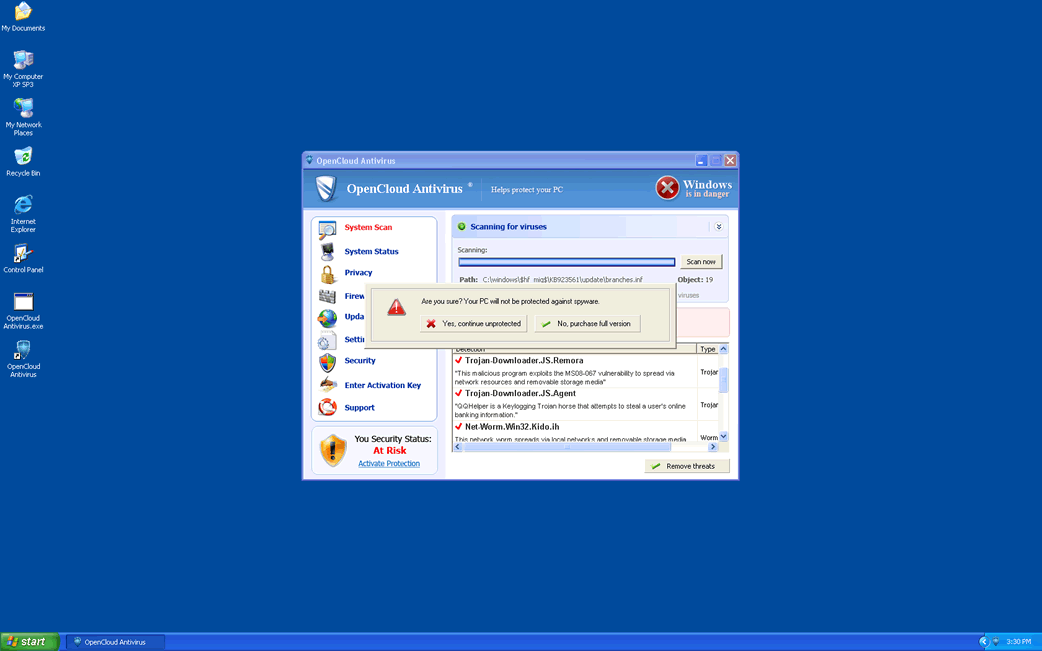
PUPs often masquerade as legitimate and harmless software, enticing users with promises of various features that may not actually work as advertised. One common example is fake anti-malware applications, which prompt users to purchase fake activation keys for non-existent functionalities.
In addition to their misleading promises, PUPs typically come equipped with data-tracking capabilities. They can collect a range of sensitive information, including browsing and search history, Internet cookies, login credentials, personally identifiable details and financial data. This harvested data may then be purchased by crooks or shared with third parties, potentially including cybercriminals.
Another tactic employed by unwanted apps is intrusive advertising campaigns. These programs, known as adware, bombard users with advertisements across various interfaces. These advertisements may promote deceptive or unsafe content such as schemes, fraudulent software or even malware. Clicking on these advertisements can sometimes result in stealthy downloads or installations of additional unwanted software.
Furthermore, PUPs often possess browser-hijacking abilities. They can alter browser settings to promote fake search engines through redirects. This means that users may be redirected to these fake search engine websites when a search query is typed into the URL bar or open new tab pages. While these illegitimate search engines may appear to function, they typically fail to provide legitimate search results, often redirecting users to genuine internet search engines like Google, Bing or Yahoo.
How do PUPs (Potentially Unwanted Programs) Get Installed on Users' Devices?
PUPs employ various shady distribution tactics to infiltrate users' devices. Here's how they commonly exploit these tactics:
- Software Bundling: PUPs often piggyback on legitimate software downloads. They are bundled with popular free applications that users willingly download, such as media players, file converters, or browser extensions. During the installation process, users may overlook or rush through the prompts, inadvertently agreeing to install the bundled PUPs.
- Deceptive Advertisements and Pop-ups: PUPs may be promoted through deceptive online advertisements and pop-ups. These advertisements often masquerade as legitimate alerts, claiming that the user's device is infected or that they need to update software. Unsuspecting users may click on these advertisements, leading to the unintentional download and installation of PUPs.
- Fake Software Updates: PUPs may mimic legitimate software update notifications to trick users into downloading and installing them. These fake updates often appear when users visit dubious websites or click on malicious links. Once installed, the PUPs can perform unwanted actions on the device.
- Phishing Emails and Websites: Cybercriminals may distribute PUPs through phishing emails or websites. These emails and websites often contain enticing offers or urgent messages urging users to download attachments or click on links. Upon doing so, users inadvertently download and install the PUPs onto their devices.
- Social Engineering Tactics: PUPs may leverage social engineering tactics to manipulate users into installing them. This can include enticing offers, fake prizes or rewards, or scare tactics that create a sense of urgency. Users may be persuaded to download and install PUPs believing they are legitimate or necessary for their device's security.
Overall, PUPs exploit users' trust and lack of awareness through deceptive tactics, ultimately leading to their inadvertent installation on users' devices. Vigilance and alertness are essential to avoid falling victim to these shady distribution tactics.