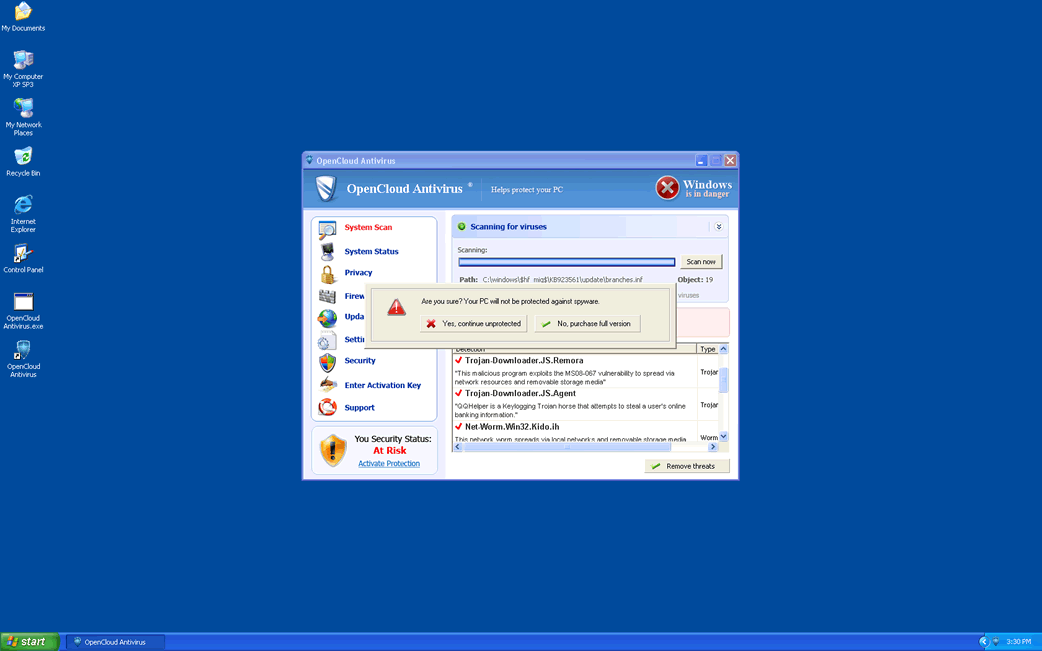
World Wide Web App
Information security researchers have discovered and analyzed an application called the 'World Wide Web.' Their analysis reveals that it is classified as a Potentially Unwanted Program (PUP). This classification indicates that the World Wide Web app is very likely to contain undesirable and potentially harmful features. Moreover, the installer for the World Wide Web app also bundles other suspicious software. Notably, this application may infiltrate systems alongside the Artificius rogue browser.
Installing the World Wide Web App May Lead to Unwanted Privacy Risks
PUPs often possess harmful capabilities. Many of these applications collect sensitive user data, such as browsing and search histories, browser cookies, login credentials (usernames and passwords), personal identification details, and financial details. This harvested data can then be sold to third parties or otherwise exploited for profit.
PUPs frequently operate as adware, displaying advertisements on various interfaces, including visited websites, desktops, and more. These ads can promote online scams, unreliable or dangerous software, and even malware. In some cases, interacting with these ads can trigger stealthy downloads or installations of additional unwanted software.
Another common feature of PUPs is their ability to hijack browsers. They can alter browser homepages, default search engines, and new tab or window URLs to direct users to specific, often untrustworthy, sites. Browser hijackers typically promote fake search engines that cannot generate legitimate search results, redirecting users instead to genuine search engines like Google, Yahoo, or Bing.
It is important to note that PUPs are often bundled with other undesirable or dangerous software. For instance, the World Wide Web application might be installed alongside Artificius, a rogue browser.
PUPs Often Exploit Questionable Distribution Techniques
PUPs often exploit questionable distribution techniques to infiltrate users' systems. Here are some of the common methods they use:
Bundling with Legitimate Software: PUPs are frequently bundled with legitimate software downloads. When users download a desired application from third-party websites, they may unwittingly install additional unwanted programs that come packaged with it. These PUPs are often pre-selected for installation in the setup wizard, making it easy for users to install them without realizing it.
Misleading Advertisements and Pop-Ups: Users may encounter misleading advertisements or pop-ups that claim their system is at risk or that a particular software is needed for optimal performance. Clicking on these ads often initiates the download of PUPs.
Fake Software Updates: PUPs can be disguised as critical software updates. Users might receive notifications or see ads claiming that their software, such as a web browser or media player, needs an urgent update. Following these prompts leads to the installation of PUPs instead of legitimate updates.
Freeware and Shareware: Freeware and shareware are often accompanied by PUPs as a way for developers to monetize their software. During the installation process, users may be prompted to accept additional "useful" tools or enhancements, which are actually PUPs.
Social Engineering: PUPs can be spread through social engineering tactics, where users are tricked into downloading and installing them. This can include phishing emails, fake tech support calls, or deceptive websites designed to look like legitimate services.
Compromised Software Repositories: Even some reputable software repositories can be compromised or host software that includes PUPs. Users who trust these sources might end up with unwanted programs if they don't carefully review the installation process.
By using these and other deceptive distribution techniques, PUPs manage to infiltrate users' systems, often without their explicit consent or knowledge. This underscores the importance of a careful online behavior and thorough scrutiny of any software installation process.